Okta
Configure Voilà for Okta
Create a new Application
Type: SAML 2.0
App Name: Voila
Configure SAML Settings
Audience (Entity ID): https://api.voila.live/sso/saml
Single Sign On URL: https://api.voila.live/sso/saml/init
Recipient URL: https://api.voila.live/sso/saml/consume
Response: Signed
Assertion Signature: Signed
Signature Algorithm: RSA_SHA256
Relay state: None
Logout URL: Disabled
Signature Certificate: Upload this pem file below
Application Profile
- Go to
Directory > Profile Editor - Edit the
Voilàapplication - Create new
Application attributes
| Okta Application attribute |
|---|
| family_name |
| given_name |
| sub |
| sharePersonalData |
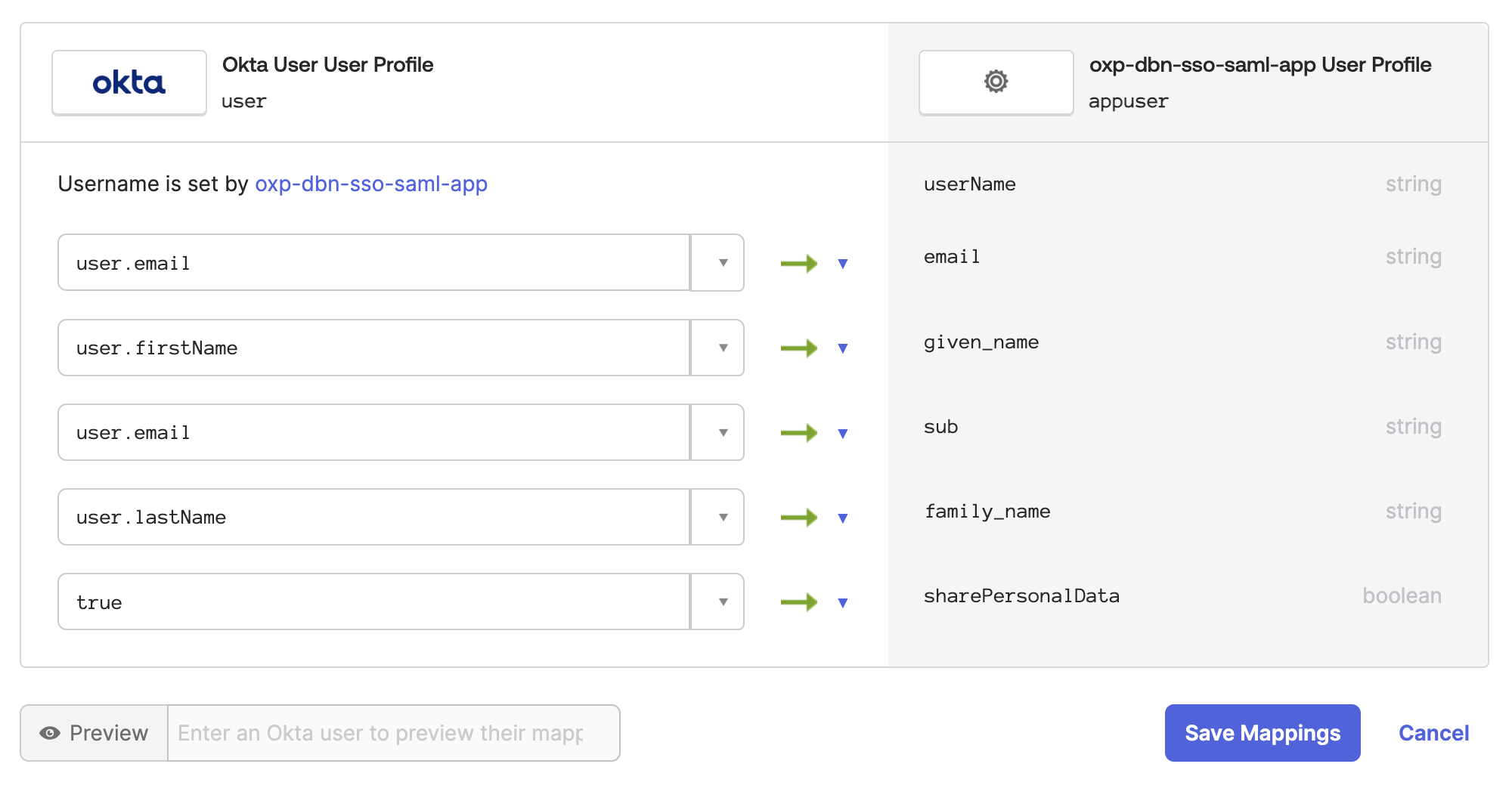
- Map the new
Application attributestoOkta User attributes
| Okta Application attribute | Okta User attribute |
|---|---|
| family_name | user.lastName |
| given_name | user.firstName |
| user.email | |
| sub | user.email |
| sharePersonalData | true (constant, see GDPR related paragraph) |
Attributes and claims
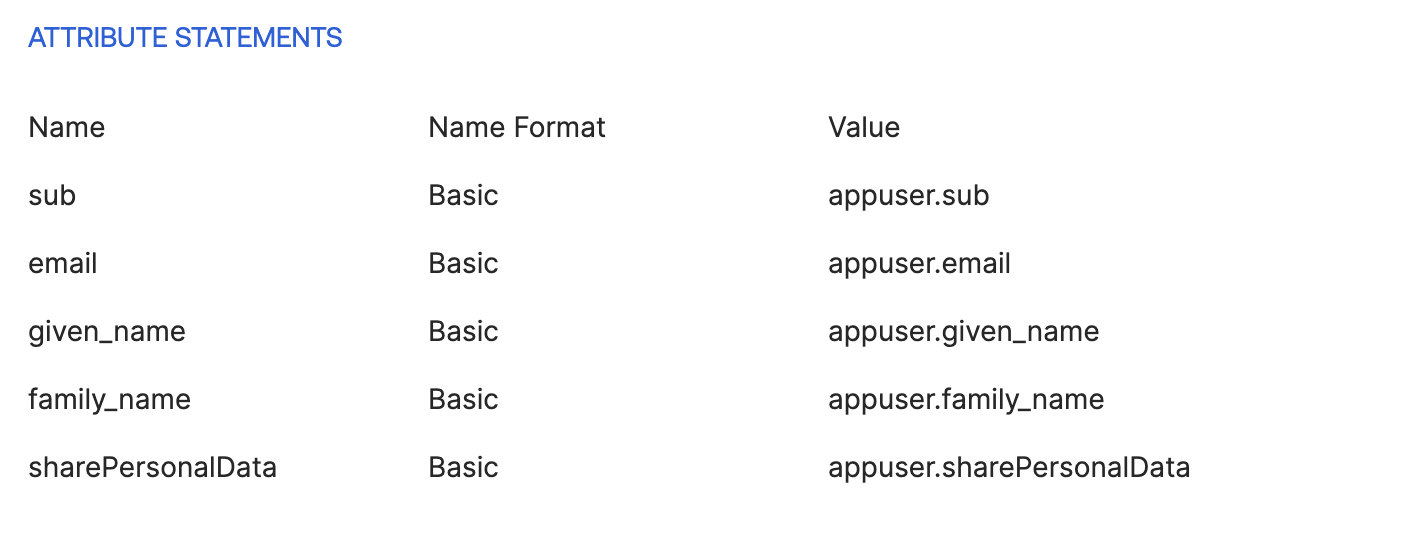
- Remove any previous mapping
- Add the following mapping
| Okta Application attribute | Voilà attribute |
|---|---|
| appuser.family_name | family_name |
| appuser.given_name | given_name |
| appuser.email | |
| appuser.sub (or any field whose value is unique, ex: employeeId) | sub |
| appuser.sharePersonalData | sharePersonalData |
What about the GDPR ?
Using the SSO feature has impacts on your GDPR compliance. Indeed, harvesting the user’s consent must be done by your organization and prior to your event.
Activating the SSO will prevent the player to display any kind of form at signup